CVE-2019-8577
Information
Utilizing CVE-2019-8602 and query hijacking we are able to bypass secure boot and achieve iOS persistencey.
Replacing one of the commonly used databases with a malicious version, the contacts db in our example.
After the device reboots and our malicious database is queried, we re-gain code execution.
As many databases are shared among several users with varying permissions it is also possible to elevate privileges.
Available for: iPhone 5s and later, iPad Air and later, and iPod touch 6th generation
Impact: An application may be able to gain elevated privileges
Description: An input validation issue was addressed with improved memory handling.
Crash Dump:
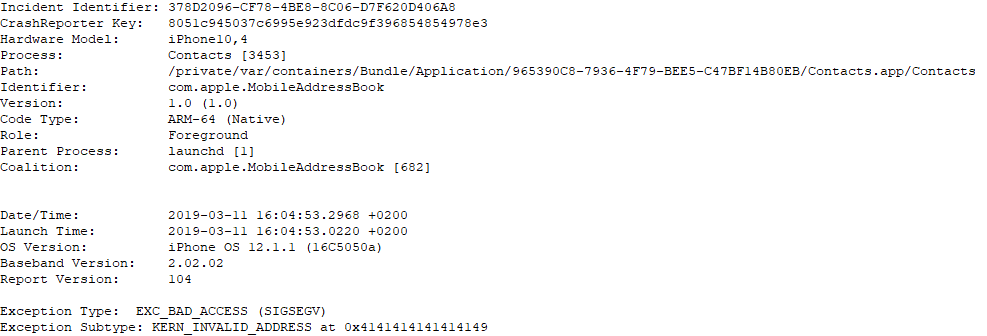
Poc:
Attached
Attachments:
crash.png
AddressBook.sqlitedb.pwn
References:
https://support.apple.com/en-us/HT210118
https://support.apple.com/en-us/HT210119
https://research.checkpoint.com/select-code_execution-from-using-sqlite/